

by T.L.Ford, 2010
Website: Cattail.Nu
Email: T@Cattail.Nu
Study for the CISSP certification exam the way your Brain prefers...
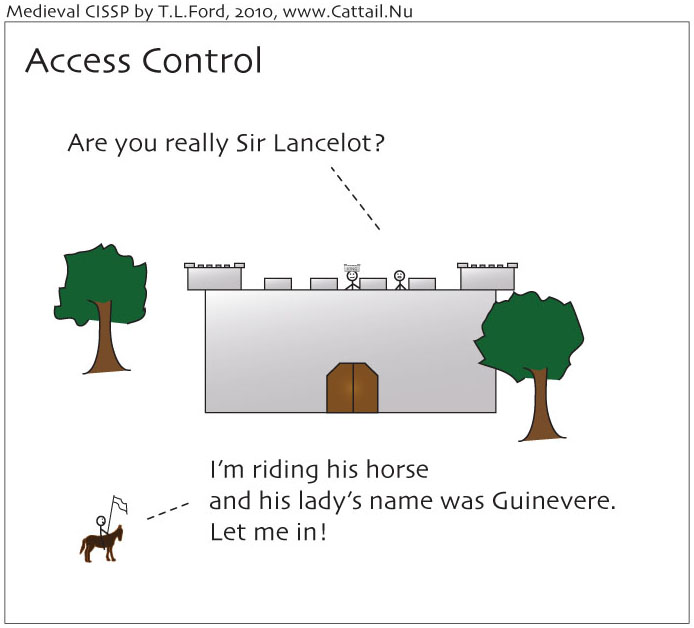
Access Control: Strong Authentication

Legal, Regulations, Investigations, and Compliance
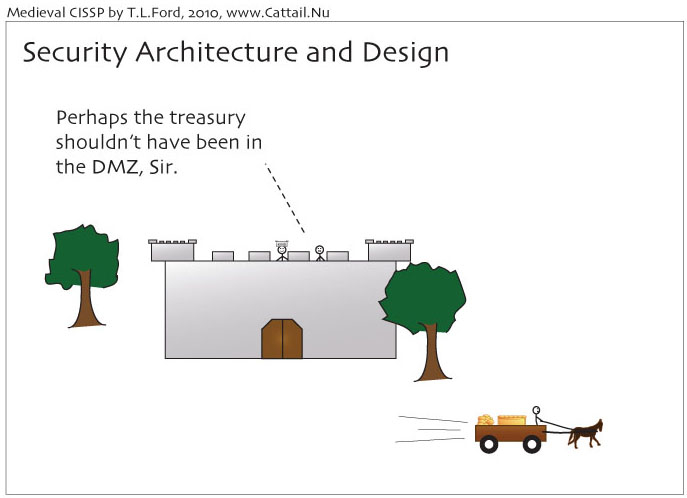
Security Architecture and Design
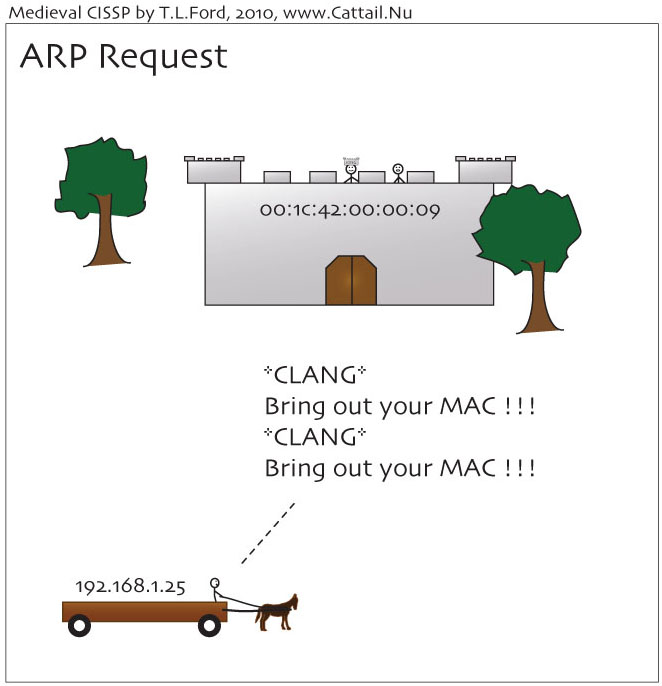
Address Resolution Protocol (ARP) Request
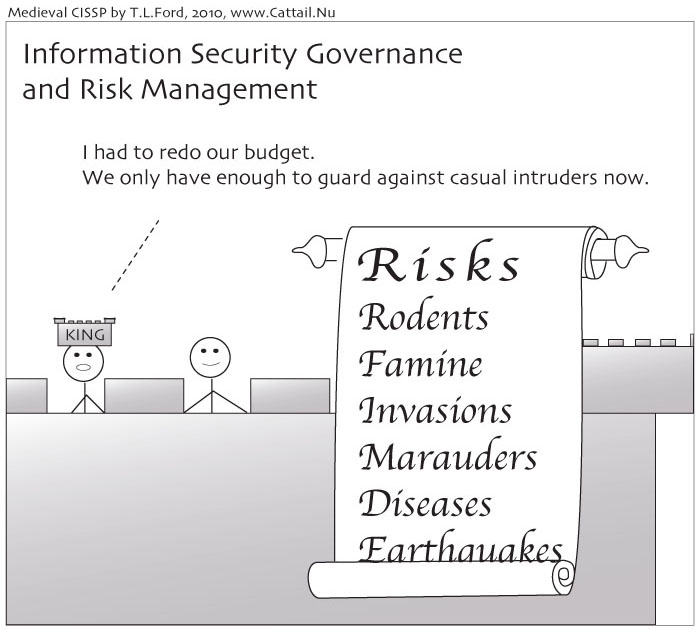
Information Security Governance and Risk Management
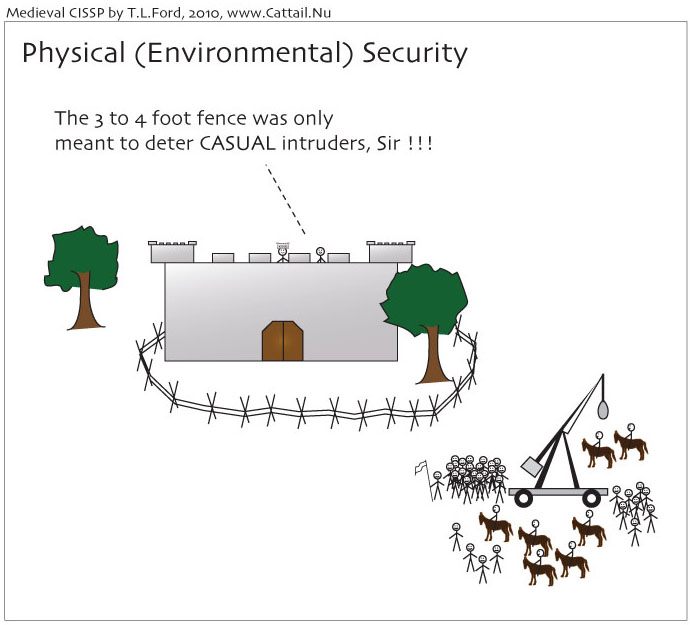
Physical (Environmental) Security
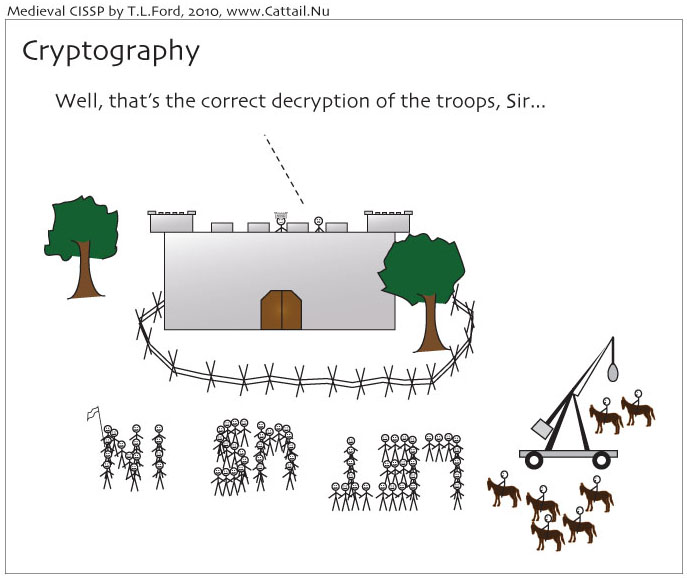
Cryptography
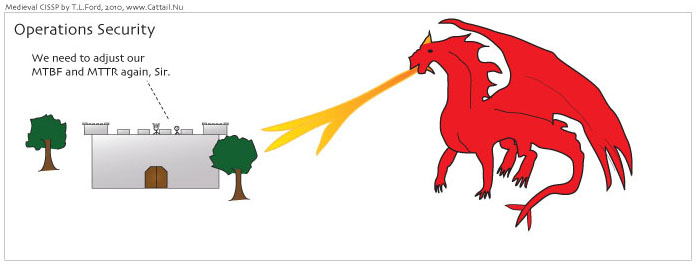
Operations Security: Mean Time Between Failures (MTBF) and Mean Time To Repair (MTTR)

Business Continuity and Disaster Recovery Planning
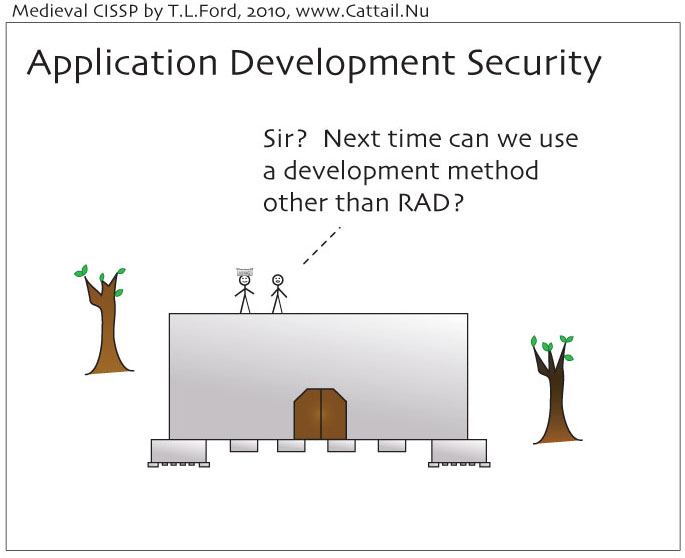
Application Development: Rapid Application Development (RAD)
Telecommunications and Network Security: OSI Model
(or "Chapter 7: Telecommunications and Network Security" rewritten to be much shorter and wildly inaccurate for the sake of humor)
In the beginning, people carved stuff onto stone tablets, but that wasn't working out so well.
So the Thinkers got together and thought up a computer.
The Builders saw that this was good and built many, but they needed to talk to each other. So the Builders, not being much on aesthetics, merely stuck another wire into the back of the computer. And everyone in the room was happy.
Then Manufacturers came along and said, "Hey! We want to make money by creating our own hardware." But there were many of them and they each wanted to do their own thing.
How could computers talk if all the parts worked different? The Thinkers eventually worked out something called the OSI Model which sorted out the 1's and 0's. But this did not stop the Manufacturers from screwing around and doing stuff their own way that maximized profit and guaranteed a monopoly.
Thus the Thinkers huddled together for protection and created a bunch of Protocols to teach everyone how the 1's and 0's should be organized. Just so no one would feel bad or left out (and so that they would actually feel a responsibility for these rules and therefore have an obligation to obey them), they published these protocols under the name "RFC"s, which stands for "Request for Comments".
Unfortunately, people thought that meant the Thinkers actually wanted feedback, so many RFCs were eventually obsoleted, modified, and generally made into long, obnoxious way-too-technical documents. Several annoyed Thinkers slipped in some bits of humor, but this got mostly stamped out.
The Manufacturers started following the rules, but to be competitive and sell more stuff, kept coming up with newer, better, faster, longer, greater stuff (this was before improvements meant just adding more salt and high fructose corn syrup and a prettier label). As soon as one Manufacturer came out with something, someone else would "borrow" the idea and create their own. And of course, theirs wouldn't work exactly the same.
The Thinkers sighed. That whole RFC thing for the Protocols was way out of hand by this point, so they decided to create a new set of rules for how hardware needed to work, and they called these Standards. And just to make certain no one confused these with that whole too-many-cooks-in-the-kitchen-giving-feedback thing, they decided to use a decimal numbering scheme. This means that one day, we might see "RFC 1 billion 468 thousand 246, obsoleted by RFC 2 billion 506 thousand, 801", but we'll still see Ethernet as IEEE 802.3.
Then Manufacturers came up with Repeaters, to make the the electrical signals go farther. (Remember that electrical signals get turned into 1's and 0's by Standards.)
But now that signals could cross a lot of distance, there was the problem of too many groups of computers that wanted to talk and they all needed to identify each other. The MAC addresses alone weren't good enough, because the computers couldn't find each other efficiently with so many computers. The RFC people, being in charge of how the 1's and 0's are organized, decided to use 32 bits because that would be plenty if they sorted them using something they called Masking and split them up into Class A, B, C, D, and E addresses, and set aside some for "local traffic only". (And just to be sure they always had some for themselves, they set aside the Class E ones for Research purposes only.) Subnets were born and given IP addresses.
Manufacturers then created Bridges to make the signals go farther AND sort them out a bit. And Routers to really get down to the task of sorting. And Switches to sort even faster. They even combined things to make 2000 page operations manuals, which a few people peered at looking for pictures and even less people read.
For a while, everyone was happy. Everyone who did not have a computer got one. There were even people like the OLPC (one laptop per child) folks giving away computers to make sure this happened. 32 bits for addresses wasn't enough. So the Thinkers came up with IPv6 which has 128 bits (they aren't taking any chances this time on it being too small). After much RFC'ing and sorting, they're pretty happy with it and are trying to get the Manufacturers to fully implement it. IPv6 even has some Security included, because Bad Guys came along.
Bad Guys do Bad Things to the Good Guys' Networks. They read all the Protocols and Standards very carefully and come up with ways to use them for their own profit and entertainment. Everyone is throwing in their attempts at Solutions in the form of Firewalls, Intrusion Detection Systems, and Certifications like the CISSP.
These Bad Guys called themselves Hackers. But the Good Guys also called themselves Hackers, so the Good Guys created the term Crackers for the Bad Guys, which the Bad Guys mostly ignored. The Protocol people declared that naming Good Guys and Bad Guys was not within their scope of organizing 1's and 0's. The Standards people didn't even bother to comment.
When the Bad Guys continued to refuse to call themselves Crackers (and the reporters kept getting it wrong anyway), the Good Guys decided to call themselves White Hats and the Bad Guys Black Hats, which sounds much classier. Then some smart aleck tossed in the term Grey Hat and made it not so classy anymore because there are 254 shades of grey in the RGB color set as well as in HSL, if only 99 in HSB (or HSV which is the same as HSB but the B people didn't like the letter B on account of too many Sesame Street episodes so they renamed it).
The people in charge of what goes in the dictionaries are still waiting for the Thinkers to form up another organization and make a definitive decision on what to call the Bad Guys. Even the computer security Certification people, who have been defining terms right and left and forcing these on everyone (like calling rows "tuples" and columns "attributes" because the words rows and columns are too un-certified sounding) are staying out of the Good Guy/Bad Guy naming debate too, on account of not wanting to piss off the Bad Guys. There is some speculation that when some Thinkers actually get around to naming Good Guys and Bad Guys, they'll use a combination of Roman numerals and letters for their numbering scheme and charge even more for annual dues than the Certification folks, because they can't tick off any country performing espionage/sabotage, or any mafia making profit, or any terrorist group destroying things, or any bored middle school kid.
Meanwhile, the telecommunication hardware and software people will keep making things newer and better (or at least renamed with added high fructose corn syrup and salt and a prettier label), and the Bad Guys (or whatever people eventually decide to call them that sticks) will continue to figure how how to do Bad Things, and database people will have to get used to calling things tuples and attributes.
To Be Continued...